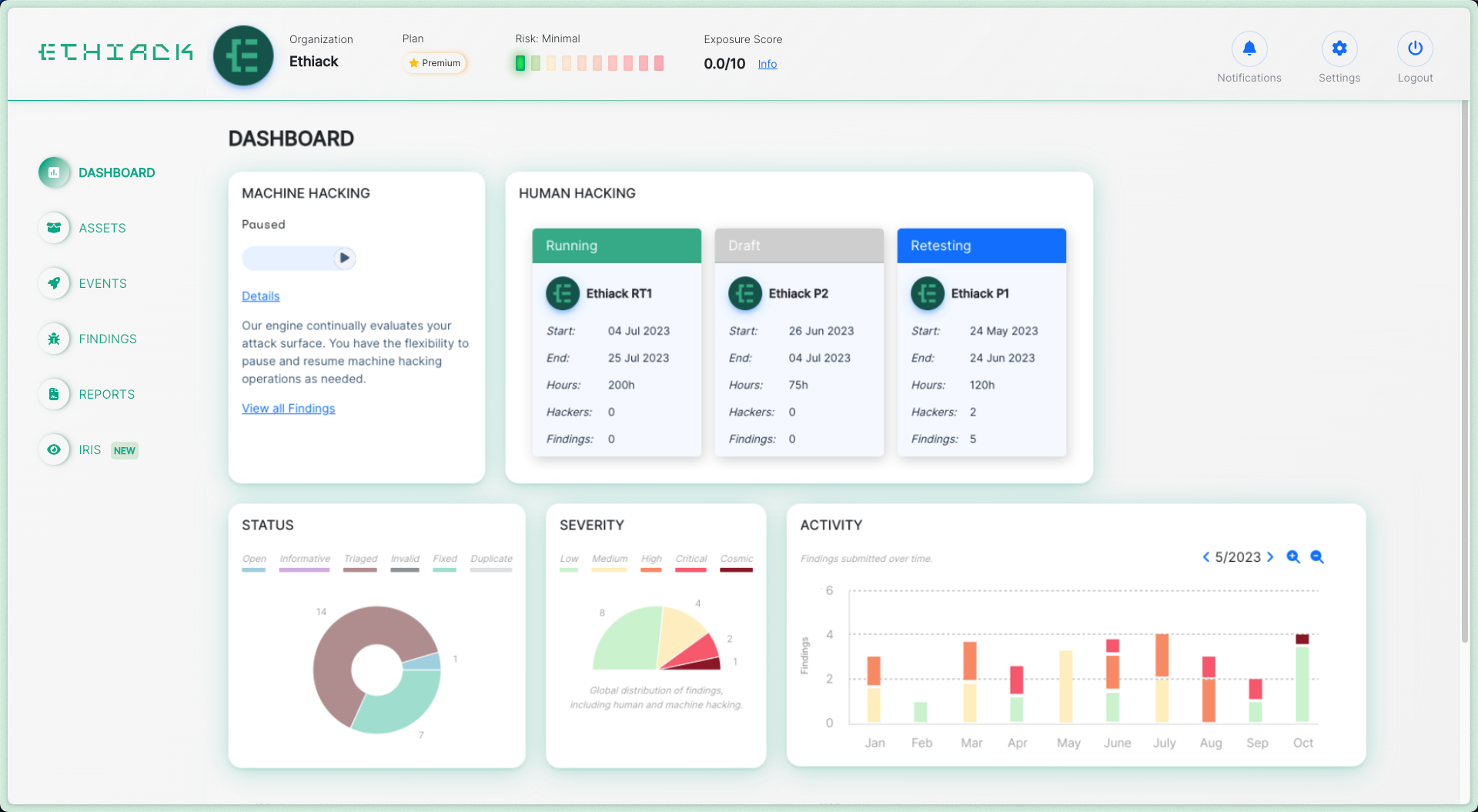
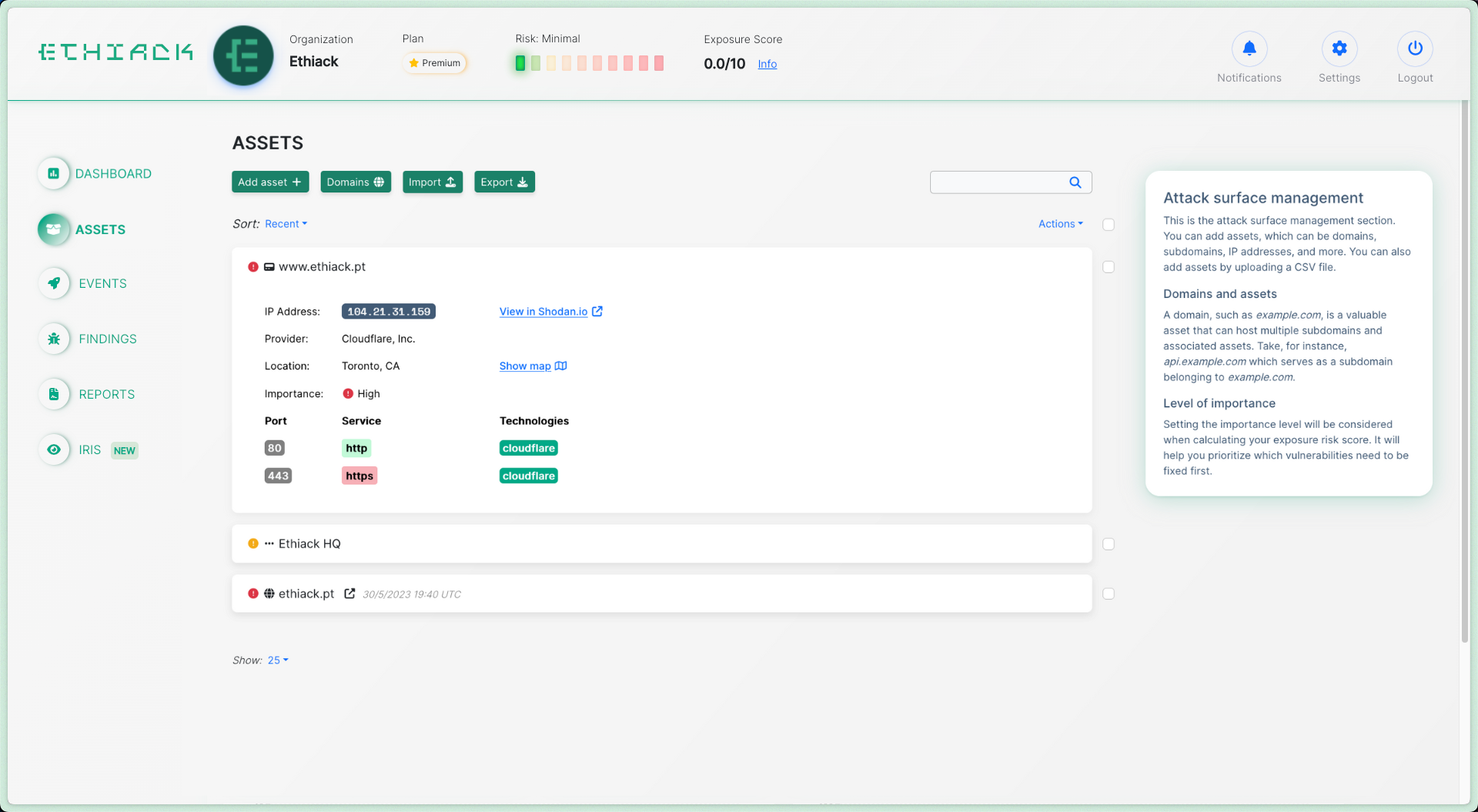
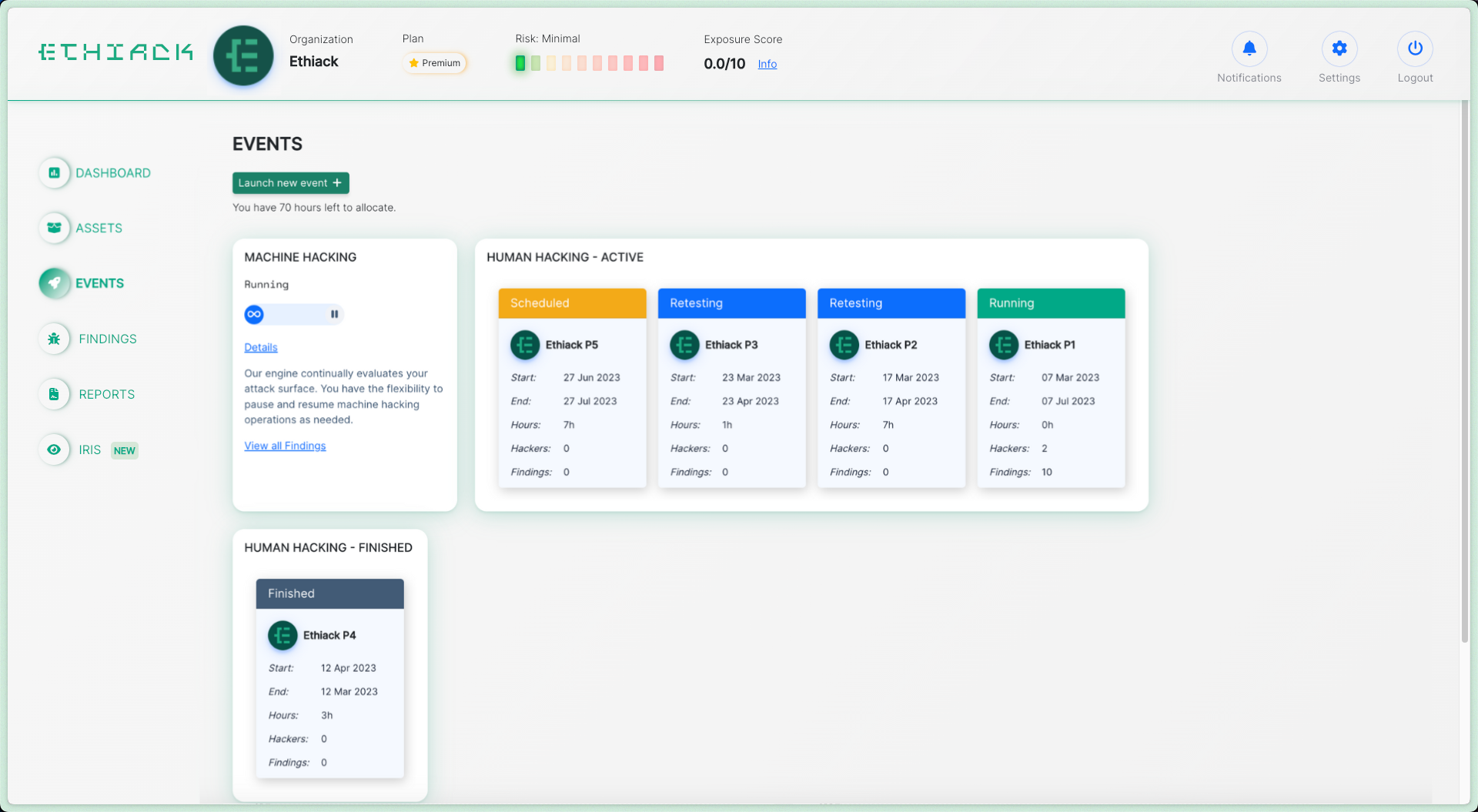
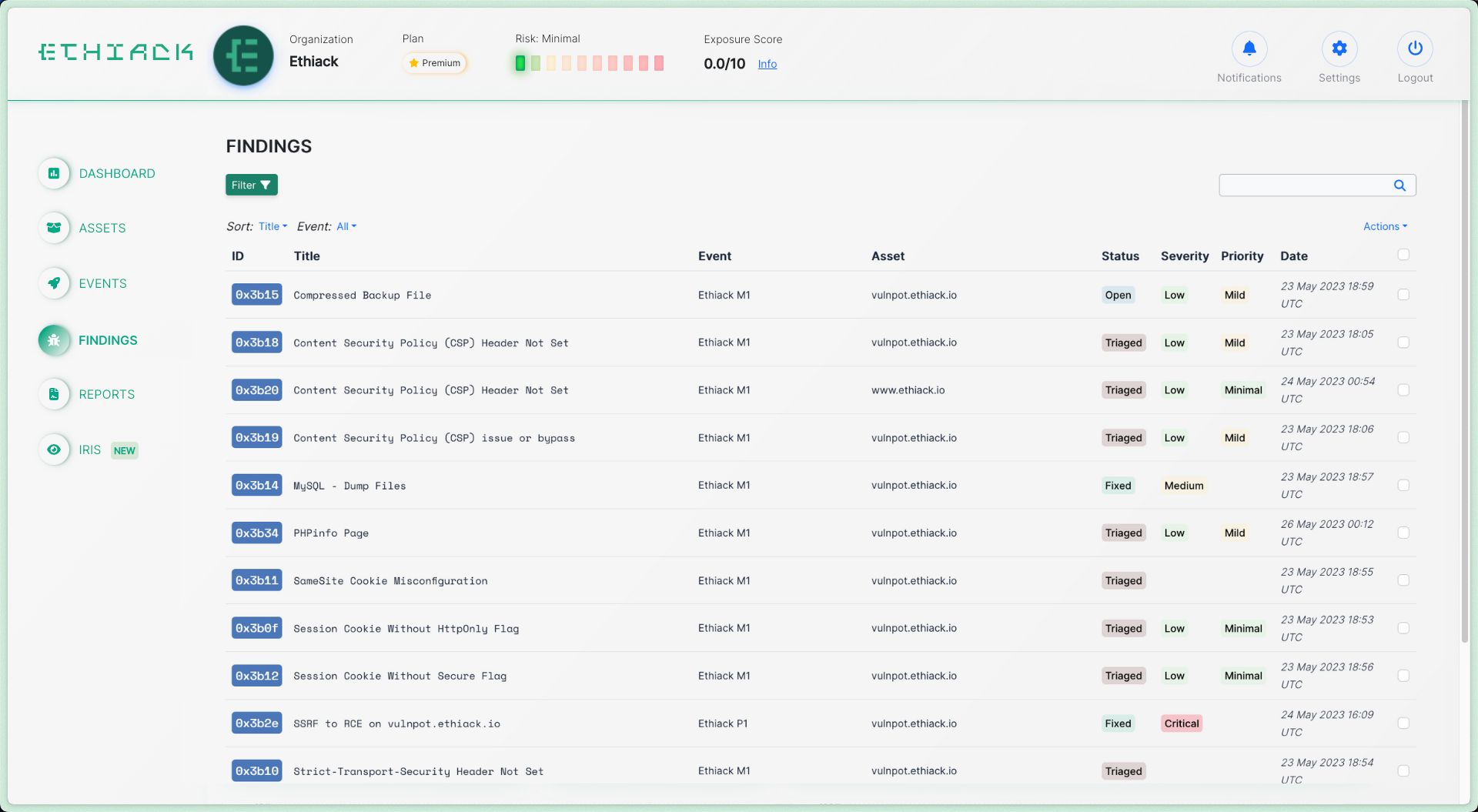
Stay Ahead of Threats with
Autonomous Pentesting
See what our customers say about us

Paulo Ribeiro
Co-founder & VP of Engineering at Smartex
"Thanks to Ethiack's autonomous hacking, Smartex is moving towards a continuous evaluation of our digital infrastructure. We can quickly identify and address vulnerabilities even with our fast frequency of development and deployment."
.png?width=760&height=760&name=TESTEMUNHO%20BALADAPP%20(1).png)
Wagner Caixeta
Partner & CTO at BaladAPP
"We continuously receive reports on vulnerabilities, including detailed guides on exploitation and mitigation. Learning how attacks happen allows us to develop products with greater security. We had a massive transfer of knowledge. I highly recommend it."
.png?width=760&height=760&name=TESTEMUNHO%20(1).png)
André Alves
Senior DevOps at ComplianceWise
"Ethiack remains our stalwart guardian, upholding the integrity of our digital assets. It's real-time monitoring and comprehensive testing ensure no vulnerability goes unnoticed. Ethiack's user-friendly interface and strategic insights allow us to prioritize actions, take proactive measures, and optimize resources."

André Araújo
SecOps Engineer at CEGID
"The way Ethiack incorporates EASM with Automated Pentesting has brought us simplicity and proactivity in solving large-scale problems. As a group with many exposed assets, doing this work manually was impossible. The main transformation was gaining a complete view of our surface, which we previously lacked. What we have publicly exposed, their vulnerabilities, and our impact in cyberspace."
See Ethiack in Action
Book a personalized demo to see Ethiack in action, get tailored answers to your questions, and learn how autonomous pentesting can secure your organization.
What you’ll get from this 15-min demo:
-
Discover how Ethiack delivers continuous, autonomous pentesting powered by AI and hacker expertise;
-
See how you can identify and prioritize real, exploitable risks—across external and internal assets;
-
Understand how Ethiack helps you stay compliant with standards like ISO 27001, SOC 2, and more—automatically.
-2.png?width=469&height=50&name=v1_%20(2)-2.png)



.png?width=769&height=284&name=Design%20sem%20nome%20(21).png)


.png?width=769&height=284&name=logos%20website%20(4).png)
.png?width=769&height=284&name=logos%20website%20(2).png)
.png?width=769&height=284&name=logos%20website%20(3).png)



.png?width=769&height=284&name=prozis-logo%20(2).png)

.png?width=769&height=284&name=logos%20website%20(10).png)